
Note: The following post was originally published on the Secjuice blog.
What comes to mind when you hear “cybersecurity”? A pentester? Security researcher? Compliance officer? IT Support? MSSP? EDR? “Cybersecurity” has a multitude of meanings. Almost every company wants a “cybersecurity expert,” but what does that even mean? What skills are those companies looking for in a candidate?
Major distractors and impediments to seeking and finding such a person or role reside in a conflation of terms. What does someone mean when they say they need a cybersecurity expert? What does a cybersecurity skillset entail? (1)
The term could mean the technical aspects of information security (e.g., packet inspection, Nmap, malware analysis, threat hunting). It could entail the usual aspects of a sysadmin’s duties (e.g., access control, permissions, firewall config, server auditing). Perhaps it refers to what someone in tech support does every day (e.g., workstation imaging and deployment, disabling access when an employee leaves)? Maybe it means the umbrella terms of Information Assurance or Information Security.
It could even mean a skill set involving GRC (governance, risk, compliance).
This link has an excellent map of the Cybersecurity domains, it’s entitled Cybersecurity Domains, but is it “Cybersecurity?” Or is it “Information Security?”
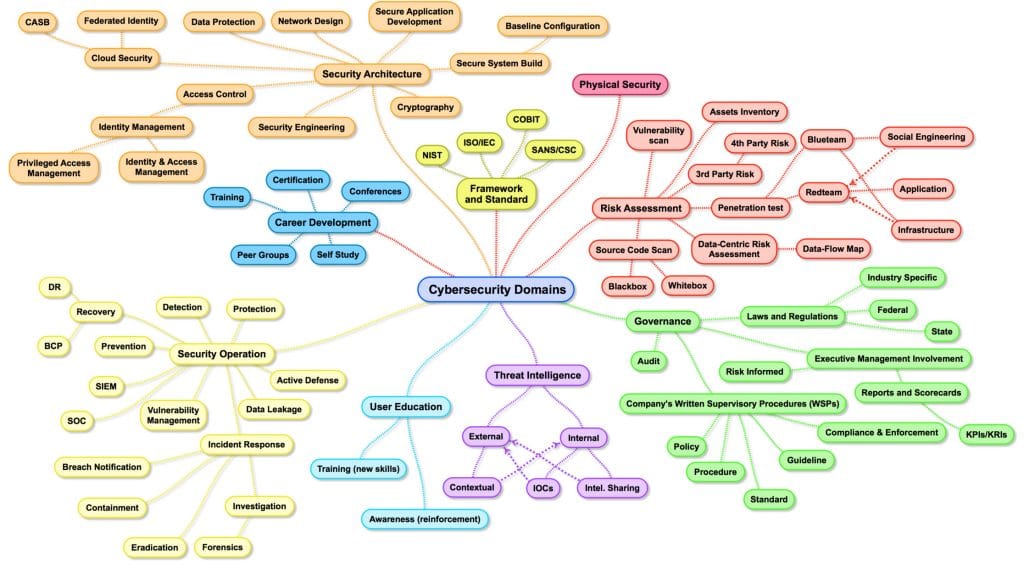
What are the Implications?
The areas referenced above are each and all vital aspects of securing the online world. And each connotation involves different, even widely varying, skill sets. These variations on a theme create significant issues, both for those looking for jobs and those looking to fill jobs.
A business leader might think of cybersecurity in the technical aspect of securing their IT infrastructure. When looking for a new position and not wanting to sound outdated, they may look for a “cybersecurity” expert, whereas what they truly need is someone who is more qualified as a sysadmin/tech support.
Maybe the org is looking for someone with a cybersecurity title or cert in their skillset, while the candidate, truly able to do the actual job required, only appears to have outdated or basic tech support skills.
HR personnel may only know what is seen in the marketing ads. They’ve been tasked by their board to find a cybersecurity expert, so HR is looking for new hires with offensive and/or technical security expertise. But what they need is a generalist with a jumble of skills.
New job seekers might not be able to translate their skills to the job descriptions. Companies might not know what they’re looking for, and are concerned that they’ll have to spend $1,000s extra a year to train a person.
Another aspect that causes confusion is that university graduates may have been told that they can make a huge salary, yet the salary range reports where they live do not agree. Local orgs might need someone with more experience than the local talent pool has, perhaps even needing expertise – anything beyond just exposure.
What Else Causes Issues?
Information security is a puzzle. The dimensions of the puzzle, the number of pieces, and the complexity of the shapes are all determined by the factors such as the size of the company, the talent required, the regulations involved, and the industry. And, regardless of the puzzle, you don’t have a box top for the picture.
There’s not one single “golden image” available for infosec. People may cry “Security is broken!” This assumes that there’s an ideal picture out there that has been overlooked. Who’s to say whether you need Splunk or not? What’s the best solution for 2FA? Does the org need biometrics? Is on-prem or cloud better? Maybe hybrid? Linux or Windows?
What Can Be Done?
A task for job-seekers is to go line-by-line through the job description and figure out if they have Exposure, Experience or Expertise for each line. That’s one way to weed through the jargon. Another step is to get in front of those who hire at a conference or a job fair (once quarantine and social distancing rules are lifted, of course). Potentially nerve-wracking? Yes. Effective? More so than being just an avatar and a PDF.
On the grander scale, it’s important to note that there are some foundational pieces to the infosec puzzle (e.g., corners and edges), but even these aren’t a must-have for all because there are so many factors that are possible (think of a circular puzzle – all edges, no corners). These pieces include, but are not limited to: regulated industry, types of data that needs to be protected, points of data entry, building size, number of employees, and geographical regions.
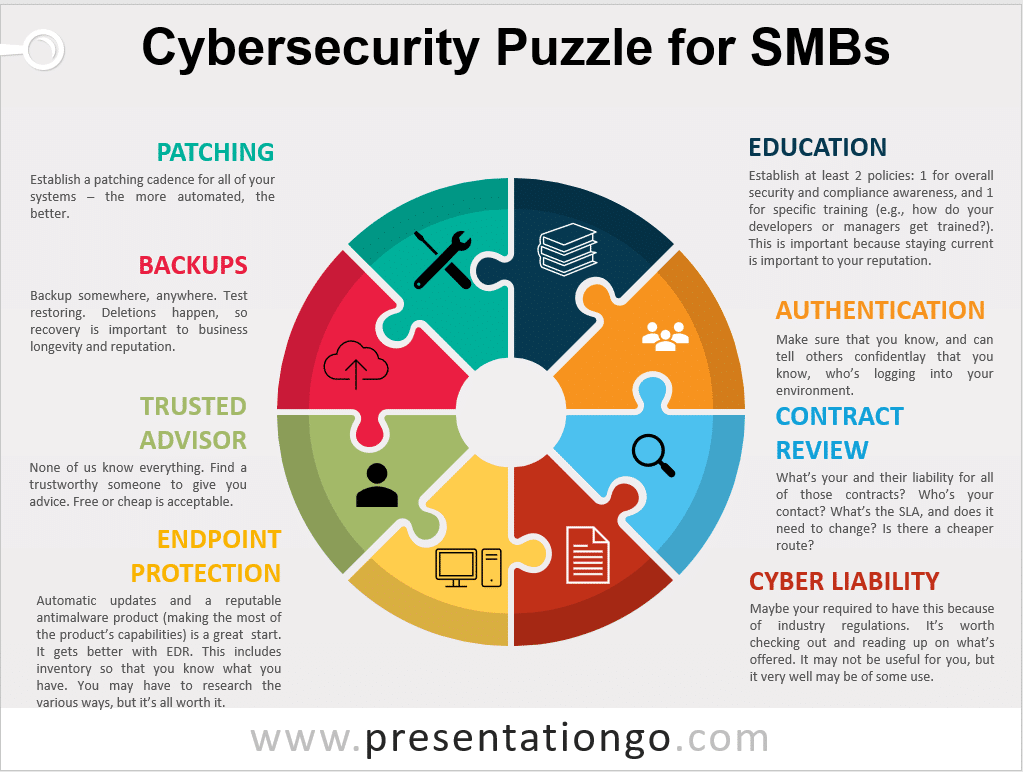
This puzzle is a place to start. One can use it to start to get a handle on what’s needed in the company, or to see where one has some skills that apply to the necessary aspects or corporate security.
Here are the pieces:
- Patching
- Backups
- Trusted Advisor
- Endpoint Protection
- Education
- Authentication
- Contract Review
- Cyber Liability
All the best to you in finding a fulfilling role or candidate. Stay safe!
(1) see Page 13 of (ISC)2’s 2019 Workforce Report
About The Author

- Ross Moore is the Cyber Security Support Analyst with Passageways. He was Co-lead on SOC 2 Type 1 implementation and Lead on SOC 2 Type 2 implementation, facilitated the company's BCP/DR TTX, and is a HIPAA Security Officer. Over the course of his 20 year IT career, Ross has served in a variety of operations and infosec roles for companies in the manufacturing, healthcare, real estate, business insurance, and technology sectors. He holds (ISC)2’s SSCP and CompTIA’s Security + certifications, a B.S. in Cyber Security and Information Assurance from WGU, and a B.A. in Bible/Counseling from Johnson University.


